描述
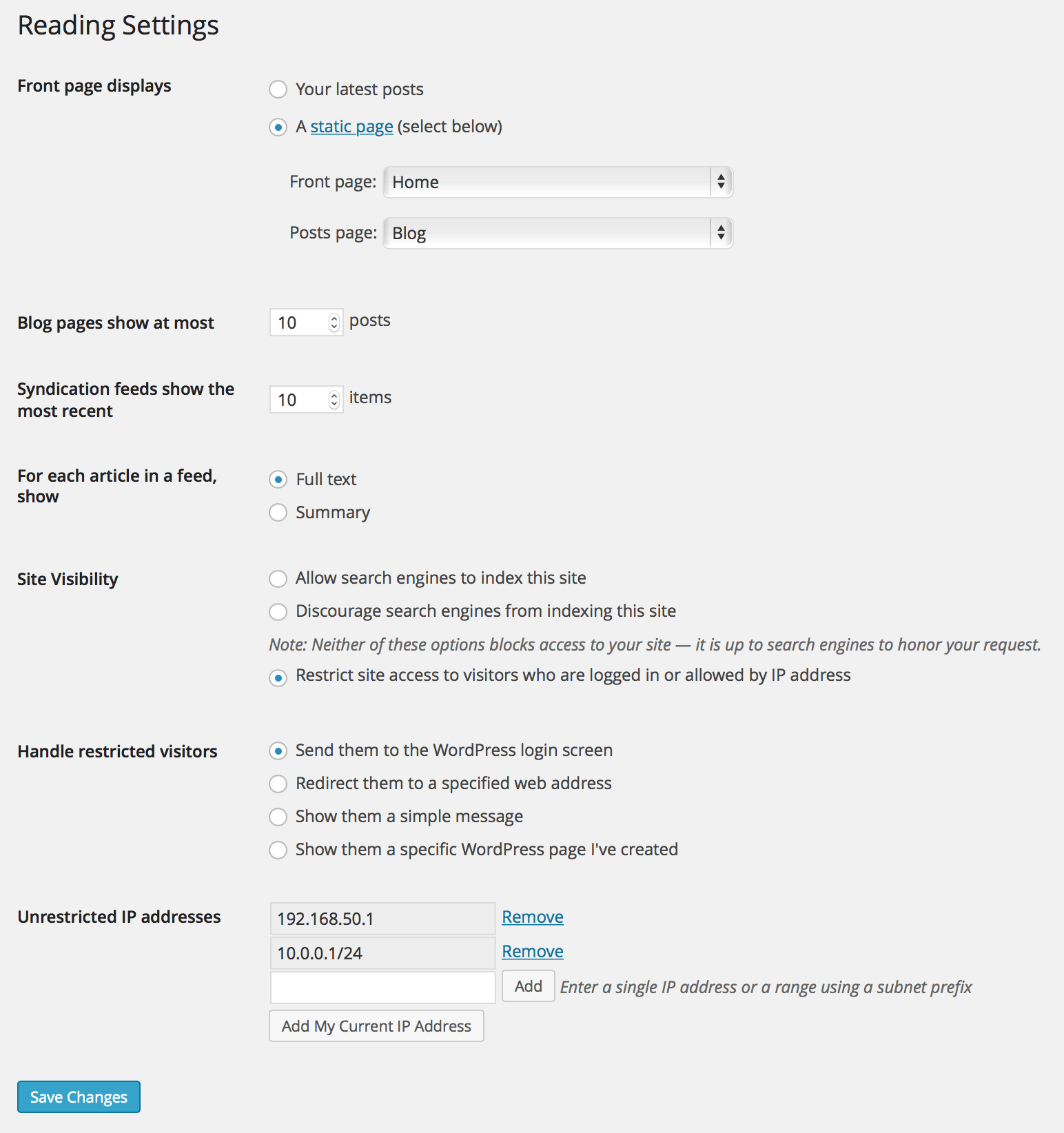
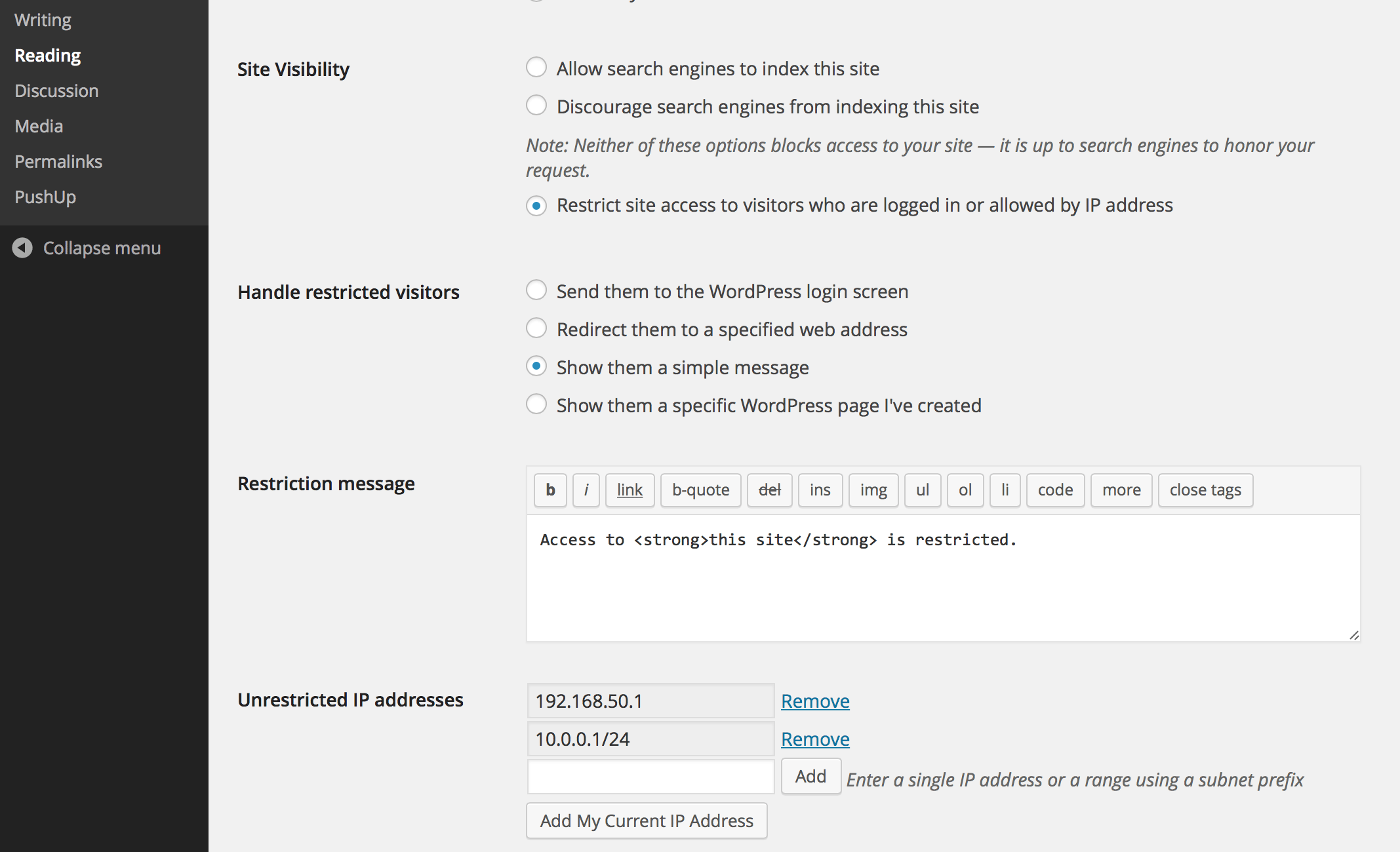
Limit access your site to visitors who are logged in or accessing the site from a set of specified IP addresses. Send restricted visitors to the log in page, redirect them, or display a message or page. A great solution for Extranets, publicly hosted Intranets, or parallel development / staging sites.
Adds a number of new configuration options to the Reading settings panel as well as the Network Settings panel in multisite. From these panels you can:
- Enable or disable site restriction
- Change the restriction behavior: send to login, redirect, display a message, display a page
- Add IP addresses to an unrestricted list, including ranges
- Quickly add your current IP to the unrestricted list
- Customize the redirect location, including an option to send them to the same requested path and set the HTTP status code for SEO friendliness
- Define a simple message to show restricted visitors, or select a page to show them – great for “coming soon” teasers!
螢幕截圖
安裝
- Install easily with the WordPress plugin control panel or manually download the plugin and upload the extracted folder to the
/wp-content/plugins/directory. - Activate the plugin through the ‘Plugins’ menu in WordPress.
- Configure the plugin by going to the “Reading” menu (WP3.5+) or “Privacy” (earlier versions) under “Settings”.
常見問題
-
Where do I change the restriction settings?
-
Restricted Site Access settings are added to the Reading page, with WordPress’s built in site privacy options. (It was moved there from a separate Privacy settings page in 3.5.)
-
It’s not working! My site is wide open!
-
Most commonly, Restricted Site Access is not compatible with some page caching solutions. While the plugin hooks in as early as it can to check visitor permissions, its important to understand that some page caching plugins generate static output that prevents plugins like Restricted Site Access from ever checking individual visitors.
To the extent that sites blocked by this plugin should not need to concern themselves with high scale front end performance, we strongly recommend disabling any page caching solutions while restricting access to your site. Keep in mind that most page caching plugins do not cache the “logged in” experience, anyhow. Also note that the plugin is fully compatible with other caching layers, like the WordPress object cache.
-
How do I allow access to specific pages or parts of my site?
-
Developers can use the
restricted_site_access_is_restrictedfilter to override normal restriction behavior. Note that restriction checks happen before WordPress executes any queries; it passes the query request from the global$wpvariable so developers can investigate what the visitor is trying to load.For instance, to unblock an RSS feed, place the following PHP code in the theme’s functions.php file or in a simple plug-in:
add_filter( 'restricted_site_access_is_restricted', 'my_rsa_feed_override', 10, 2 ); function my_rsa_feed_override( $is_restricted, $wp ) { // check query variables to see if this is the feed if ( ! empty( $wp->query_vars['feed'] ) ) { $is_restricted = false; } return $is_restricted; } -
How secure is this plug-in?
-
Visitors that are not logged in or allowed by IP address will not be able to browse your site (though be cautious of page caching plugin incompatibilities, mentioned above). Restricted Site Access does not block access to your “real” files, so direct links to files in your media and uploads folder (for instance) are not blocked. It is also important to remember that IP addresses can be spoofed. Because Restricted Site Access runs as a plug-in, it is subject to any other vulnerabilities present on your site.
Restricted Site Access is not meant to be a top secret data safe, but simply a reliable and convenient way to handle unwanted visitors.
In 7.3.2, two new filters were added that can be utilized to help prevent IP spoofing attacks. The first filter allows you to set up a list of approved proxy IP addresses and the second allows you to set up a list of approved HTTP headers. For any sites that were using Restricted Site Access prior to version 7.5.0, a handful of HTTP headers are trusted by default. To change this, utilize the
rsa_trusted_headersfilter to modify the HTTP headers you want to trust. If your site is not running behind a proxy, we recommend doing the following:add_filter( 'rsa_trusted_headers', '__return_empty_array' );This will then only use the
REMOTE_ADDRHTTP header to determine the IP address of the visitor. This header can’t be spoofed, so this will increase security. Note that this is now the default for all new installs since version 7.5.0.If your site is running behind a proxy (like a CDN), you usually can’t rely on the
REMOTE_ADDRHTTP header, as this will contain the IP address of the proxy, not the user. If your proxy uses static IP addresses, we recommend using thersa_trusted_proxiesfilter to set those trusted IP addresses:add_filter( 'rsa_trusted_proxies', 'my_rsa_trusted_proxies' ); function my_rsa_trusted_proxies( $trusted_proxies = array() ) { // Set one or more trusted proxy IP addresses. $proxy_ips = array( '10.0.0.0/24', '10.0.0.0/32', ); $trusted_proxies = array_merge( $trusted_proxies, $proxy_ips ); return array_unique( $trusted_proxies ); }And then use the
rsa_trusted_headersfilter to set which HTTP headers you want to trust. Consult with your proxy provider to determine which header(s) they use to hold the original client IP:add_filter( 'rsa_trusted_headers', 'my_rsa_trusted_headers' ); function my_rsa_trusted_headers( $trusted_headers = array() ) { // Set one or more trusted HTTP headers. $headers = array( 'HTTP_X_FORWARDED', 'HTTP_FORWARDED', ); return $headers; }If your proxy does not use static IP addresses, you can still utilize the
rsa_trusted_headersfilter to change which HTTP headers you want to trust. -
I received a warning about page caching. What does it mean?
-
Page caching plugins often hook into WordPress to quickly serve the last cached output of a page before we can check to see if a visitor’s access should be restricted. Not all page caching plugins behave the same way, but several solutions – including external solutions we might not detect – can cause restricted pages to be publicly served regardless of your settings.
-
Why can’t logged-in users see all the sites on my multisite instance?
-
In 6.2.0, the behavior in a multisite install changed from allowing any logged-in user to see a site to checking their role for that specific site. This is a safer default given the varying ways multisite is used; however, if you would prefer to rely on the previous behavior rather than explicitly adding users to each site, place the following PHP code in the theme’s functions.php file or in a simple plug-in:
add_filter( 'restricted_site_access_user_can_access', 'my_rsa_user_can_access' ); function my_rsa_user_can_access( $access ) { if ( is_user_logged_in() ) { return true; } return $access; } -
Is there a way to configure this with [WP-CLI](https://make.wordpress.org/cli/)?
-
As of version 7.0.0, CLI integration has been added. To see the available commands, type the following in your WordPress directory:
$ wp rsa -
How can I programatically define whitelisted IPs?
-
In 7.0.0, the capacity to define a pipe delimited array of whitelisted IP addresses via constant was introduced.
In your
wp-config.phpfile, you can define the following:define( 'RSA_IP_WHITELIST', '192.0.0.1|192.0.0.10' );In 7.1.1, the capacity to programmatically add / remove / set access IPs programmatically was introduced.
The following are valid statements:
Set IPs, ignoring all stored values (but not the constant defined values), if you’re going to use the approach with array indices rather than mixing the two.
Restricted_Site_Access::set_ips( array( '192.168.0.1', '192.168.0.2', '192.168.0.3' ) ); Restricted_Site_Access::set_ips( array( 'labelfoo' => '192.168.0.1', 'labelbar' => 192.168.0.2', 'labelbaz' => 192.168.0.3' ) );Add IPs, if they’re not already added.
Restricted_Site_Access::append_ips( array( '192.168.1.5' => 'five', '192.168.1.6' => 'six' ) );Remove IPs, if they are in the list.
Restricted_Site_Access::remove_ips( array( '192.168.1.2','192.168.1.5','192.168.1.6', ) ); -
Is there a constant I can set to ensure my site is (or is not) restricted?
-
As of version 7.1.0, two constants were introduced that give you the ability to specify if the site should be in restricted mode.
You can force the plugin to be in restricted mode by adding the following to your
wp-config.phpfile:define( 'RSA_FORCE_RESTRICTION', true );Or to ensure your site won’t be in restricted mode:
define( 'RSA_FORBID_RESTRICTION', true );Make sure you add it before the
/* That's all, stop editing! Happy blogging. */line.Please note that setting
RSA_FORCE_RESTRICTIONwill overrideRSA_FORBID_RESTRICTIONif both are set. -
What does ‘Discourage search engines from indexing this site’ do?
-
When the ‘Discourage search engines from indexing this site’ option is enabled, it prevents search engines from indexing the site while still permitting access to regular visitors.
-
What does ‘Restrict site access to visitors who are logged in or allowed by IP address’ do?
-
When this option is activated, it serves as a barrier to all visitors except those who are authenticated (logged in) or whose IP addresses are included in the ‘Unrestricted IP addresses’ setting. This restriction applies universally, even to automated crawlers such as search engines.
評價
貢獻者及開發者
“Restricted Site Access” 是一個開源的軟體。以下的人對這個外掛作出了貢獻。
貢獻者修改日誌
7.5.0 – 2023-12-14
Note: this release changes the default behavior for new installs in regards to IP detection. This shouldn’t impact existing installs but there are two filters that can be used to change this behavior. See the readme for full details.
- Fixed: Update code snippet in the readme (props @dkotter, @jeffpaul via #291).
- Security: For new installs, ensure we only trust the
REMOTE_ADDRHTTP header by default. Existing installs will still utilize the old list of approved headers but can modify this (and are recommended to) by using thersa_trusted_headersfilter (props @dkotter, @peterwilsoncc, @dustinrue, @mikhail-net, Darius Sveikauskas via #290). - Security: Bump
axiosfrom 0.25.0 to 1.6.2 and@wordpress/scriptsfrom 23.7.2 to 26.19.0 (props @dependabot, @dkotter via #293).
7.4.1 – 2023-11-14
- Added: GitHub Action summary report for Cypress end-to-end tests (props @jayedul, @Sidsector9 via #258).
- Added:
Restricted_Site_Access::append_ips()method to add IP addresses programatically (props @Sidsector9, @faisal-alvi via #267). - Added: Repository Automator GitHub Action (props @iamdharmesh, @Sidsector9 via #273).
- Changed: Bumped WordPress “tested up to” version 6.4 (props @kirtangajjar, @Sidsector9, @qasumitbagthariya, @jeffpaul via #271, #288).
- Changed: WordPress compatibility validation library namespace (props @Sidsector9, @dkotter via #278).
- Changed: Documentation to clarify what the restricted site access & discourage search engine options do (props @lkraav, @jeffpaul, @helen, @dinhtungdu, @bmarshall511, @Sidsector9 via #262).
- Changed: Updates the Dependency Review GitHub Action to check for GPL-compatible licenses (props @jeffpaul, @Sidsector9 via #261).
- Fixed: Issue with autovivification (props @mae829, @Sidsector9 via #281, @turtlepod via #281).
- Security: Add PHP environment compatibility checker (props @vikrampm1, @Sidsector9 via #268).
- Security: Bump
word-wrapfrom1.2.3to1.2.4(props @Sidsector9 via #266). - Security: Bump
semverfrom5.7.1to5.7.2(props @Sidsector9 via #264). - Security: Bump
tough-cookiefrom4.1.2to4.1.3(props @Sidsector9 via #270). - Security: Bump
@cypress/requestfrom2.88.10to2.88.12(props @Sidsector9 via #270). - Security: Bump
postcssfrom8.4.18to8.4.31(props @Sidsector9 via #279). - Security: Bump
@babel/traversefrom7.20.0to7.23.2(props @Sidsector9 via #279). - Security: Bump
Cypressversion from10.3.0to13.2.0(props @iamdharmesh, @Sidsector9 via #276). - Security: Bump
@10up/cypress-wp-utilsversion to0.2.0(props @iamdharmesh, @Sidsector9 via #276). - Security: Bump
@wordpress/envversion from5.4.0to8.7.0(props @iamdharmesh, @Sidsector9 via #276). - Security: Bump
@babel/traversefrom 7.20.0 to 7.23.2 (props @dependabot, @Sidsector9 via #282).
7.4.0 – 2023-04-18
- Added: Support for application passwords (props @kirtangajjar, @peterwilsoncc, @Sidsector9 via #247).
- Added: Support for custom header based allow-listing (props @mikelking, @ravinderk, @dkotter, @jeffpaul via #242).
- Changed: Support Level from
ActivetoStable(props [@jeffpaul](https://github.com/jeffpaul, @Sidsector9) via #244). - Changed: Bump WordPress “tested up to” version 6.2 (props @jayedul, @Sidsector9 via #251)
- Changed: Improve Github actions workflow (props @Sidsector9, @dkotter via #227, #253).
- Fixed: Plugin settings header UX (props @barryceelen, @Sidsector9 via #236).
- Fixed: Issue that caused redirect loop (props @mikegibbons4, @Sidsector9, @cadic, @peterwilsoncc) via #221.
- Security: Run E2E tests on the final ZIP build (props @iamdharmesh, @jayedul via #249).
- Security: Bump
json5from1.0.1to1.0.2(props @Sidsector9 via #241). - Security: Bump
simple-gitfrom3.15.0to3.16.0(props @Sidsector9 via #243). - Security: Bump
http-cache-semanticsfrom 4.1.0 to 4.1.1 (props @Sidsector9 via #245). - Security: Bump
@sideway/formulafrom 3.0.0 to 3.0.1 (props @Sidsector9 via #246). - Security: Bump
webpackfrom5.74.0to5.76.1(props @Sidsector9 via #248).
7.3.5 – 2022-12-14
- Added: Show an admin notice if our autoloader doesn’t exist (props @dkotter, @pablojmarti, @shahzaib10up, @peterwilsoncc via #231).
- Fixed: Ensure we load our autoloader from the root of our plugin directory (props @dkotter, @pablojmarti, @shahzaib10up, @peterwilsoncc via #231).
- Changed: Improved performance of our E2E tests (props @Sidsector9, @iamdharmesh via #218).
- Changed: Release instructions and release ZIP building via GitHub Action (props @dkotter, @faisal-alvi via #232).
- Security: Bump
loader-utilsfrom 2.0.3 to 2.0.4 (props @dependabot via #226). - Security: Bump
simple-gitfrom 3.6.0 to 3.15.0 (props @dependabot via #230).
7.3.4 – 2022-11-01
- Fixed: Fatal error due to missing vendor directory.
7.3.3 – 2022-10-31
- Added: Support for IPv6 addresses (props @jeffpaul, @Sidsector9, @cadic).
- Added: Support for subnet range and pattern formats for IPv4 and IPv6 addresses (props @jeffpaul, @Sidsector9, @cadic).
- Added: WP VIP Coding Standards (props @peterwilsoncc, @faisal-alvi, @eflorea).
- Changed: Improved adding IP user experience via settings (props @ankitguptaindia, @dhanendran, @Sidsector9, @dinhtungdu).
- Changed: Replace Grunt with Webpack (props @cadic, @Sidsector9).
- Fixed: Missing textdomains to translatable strings (props @pedro-mendonca, @Sidsector9).
7.3.2 – 2022-08-29
Note: this release contains two new filters that we recommend using to further secure your site. See the readme for full details.
- Added: New filter –
rsa_get_client_ip_address_filter_flagsto modify the range of accepted IP addresses. - Changed: Avoid disjointed plugin settings (props @helen, @peterwilsoncc, @Sidsector9).
- Changed: Bump minimum WordPress version from 5.0 to 5.7 (props @vikrampm1, @Sidsector9, @faisal-alvi).
- Changed: Bump minimum PHP version from 5.6 to 7.4 (props @vikrampm1, @Sidsector9, @faisal-alvi).
- Security: New filters –
rsa_trusted_proxiesandrsa_trusted_headershave been added to help prevent IP spoofing attacks.
7.3.1 – 2022-06-30
- Added: PHP8 compatibility check GitHub Action (props @Sidsector9, dkotter).
- Added: Dependency security scanning GitHub Action (props @jeffpaul).
- Changed: Admin settings HTML semantics for easier testing (props @Sidsector9, @faisal-alvi).
- Changed: Bump WordPress “tested up to” version 6.0 (props @peterwilsoncc, @faisal-alvi, @cadic, @jeffpaul).
- Changed: Documentation, asset, and e2e test updates (props @Sidsector9, @iamdharmesh).
- Fixed: Check netmask range before IP is added (props @Sidsector9, @PypWalters).
- Security: Bump
minimistfrom 1.2.5 to 1.2.6 (props @dependabot). - Security: Bump
gruntfrom 1.4.1 to 1.5.3 (props @dependabot). - Security: Bump
asyncfrom 2.6.3 to 2.6.4 (props @dependabot).
7.3.0 – 2022-02-08
- Added: Ability to add, remove, and set IPs programatically (props @ivankruchkoff, @helen, @paulschreiber).
- Added: Cloudflare IP detection compatibility (props @eightam, @dinhtungdu).
- Added: WP-CLI option to modify and retrieve IP entry labels (props @Sidsector9, @dinhtungdu, @mikelking).
- Added: Acceptance and end-to-end tests (props @dinhtungdu, @helen, @jeffpaul, @Sidsector9, @cadic).
- Added: Issue management automation, JavaScript linting, and PHPUnit testing via GitHub Actions (props @jeffpaul, @Sidsector9, @dinhtungdu, @mitogh).
- Changed: Update WP-CLI code to use new API for add/remove/set IPs (props @paulschreiber, @dinhtungdu).
- Changed: Bump WordPress “tested up to” version 5.8 (props @dinhtungdu, @jeffpaul, @ankitguptaindia, @BBerg10up, @sudip-10up).
- Changed: Improved Composer configuration and support (props @kopepasah, @dinhtungdu).
- Changed: Improved documentation (props @jeffpaul, @dinhtungdu, @helen).
- Changed: The default constant
WP_TESTS_DOMAINis replaced by a new constantPHP_UNIT_TESTS_ENVto allow testing correct redirections for restricted users by Cypress end-to-end tests (props @faisal-alvi, @Sidsector9, @dkotter). - Fixed: Issue with allowed IPs and associated comments being offset (props @adamsilverstein, @helen, @ivankruchkoff).
- Fixed: Prevents new users from getting WordPress setup email, new user flow in multisite installations now work as expected (props @dinhtungdu, @wkw, @jeffpaul, @ivanlopez).
- Fixed: Ensure assets are enqueued on correct screen only (props @kopepasah, @dinhtungdu, @paulschreiber, @n8dnx).
- Fixed: Use correct variable for screen reader text (props @dinhtungdu, @lkraav).
- Fixed: Set the correct filter option value to
site_publicifRSA_FORBID_RESTRICTIONis defined (props @pabamato, @dinhtungdu). - Fixed: Prevent redirect loops when Redirect URL set on the same domain with or without Redirect to same path enabled (props @Sidsector9, @faisal-alvi, @cadic via #158).
- Fixed: Undefined key “url” warning (props @Sidsector9).
- Fixed:
Redirect to same pathsetting screen-reader-text (props @pedro-mendonca). - Fixed: No loading of JS admin scripts on the network admin page (props @Sidsector9, @dinhtungdu).
- Security: Bump
websocket-extensionsfrom 0.1.3 to 0.1.4 (props @dependabot). - Security: Bump
lodashfrom 4.17.15 to 4.17.21 (props @dependabot). - Security: Bump
rmccue/requestsfrom 1.7.0 to 1.8.0 (props @dependabot). - Security: Bump
gruntfrom 1.0.4 to 1.3.0 (props @dependabot). - Security: Bump
path-parsefrom 1.0.6 to 1.0.7 (props @dependabot).
7.2.0 – 2019-11-27
- Added: Warn and confirm before network disabling the plugin (props @pereirinha, @adamsilverstein)
- Fixed: Ensure comments associated with IPs stay associated correctly (props @adamsilverstein, @ivankk, @helen)
- Fixed: Don’t show escaped HTML in page caching notice (props @adamsilverstein, @aaemnnosttv)
- Fixed: Multisite: Avoid a redirect loop when logging in as user with no role (props @phyrax, @adamsilverstein, @roytanck, @helen, @rmccue)
7.1.0 – 2019-04-11
- Added: IP whitelist: Add a Comment field next to each IP address to help identify IP addresses added to the whitelist.
- Added: Add constants to force enable/disable restrictions. Set
RSA_FORCE_RESTRICTIONtotrueto force restriction orRSA_FORBID_RESTRICTIONto disable restriction.RSA_FORCE_RESTRICTIONwill overrideRSA_FORBID_RESTRICTIONif both are set. - Fixed: Disable individual site settings when network enforced mode is on to avoid confusion about why your settings are not being respected.
- Fixed: Correctly load admin JS.
- Fixed: Improve coding standards across plugin and introduce continuous integration linting against the WordPress coding standards. Update code to VIP Go coding standards.
- Developers: Add unit tests accross plugin. Note that when the
WP_TESTS_DOMAINconstant is set, plugin redirects are disabled. Only set this constant when running the tests. - Developers: Deploy plugin from GitHub to WordPress.org using GitHub Actions.
- Developers: Add various GitHub community files.
7.0.1 – 2018-09-06
- Bug fix: Avoid redirect loop when the unrestricted page is set to be the static front page.
- Bug fix: Fall back to the login screen if the unrestricted page is no longer published.
7.0.0 – 2018-08-30
- Feature: WP-CLI support! 🎉 Try
wp rsato get started. - Feature: Whitelist IPs via the
RSA_IP_WHITELISTconstant. - Feature: Use WordPress.org-provided language packs instead of bundled translations.
- Bug fix: Restrict “virtual pages” and allow them to be used as the unrestricted page, such as with BuddyPress.
- Bug fix: Hide settings properly when no published pages exist.
- Bug fix: Avoid double slashes in asset URLs that can lead to 404 errors.
6.2.1 – 2018-05-21
- Bug fix: Don’t redirect logged-in users viewing the site in a single site install.
6.2.0 – 2018-05-18
- Functionality change: Check user’s role on a site in multisite before granting permission.
- Feature: Alter or restore previous user permission checking with the
restricted_site_access_user_can_accessfilter. - Avoid a fatal due to differing parameter counts for the
restricted_site_access_is_restrictedfilter.
6.1.0 – 2018-02-14
- Correct a PHP notice when running PHP >= 7.1.
- Refactor logic for checking ip address is in masked ip range.
- Add PHPUnit tests validating the ip_in_mask functionality.
6.0.2 – 2018-01-29
- Add a ‘restrict_site_access_ip_match’ action which fires when an ip match occurs. Enables adding session_start() to the IP check, ensuring Varnish type cache will not cache the request.
6.0.1 – 2017-06-13
- When plugin is network activated, don’t touch individual blog visiblity settings.
- When plugin is network deactivated, set all individual blogs to default visibility.
6.0 – 2017-06-12
- Use Grunt to manage assets.
- Network settings added for management of entire network visibility settings.
- Display warning if page caching is enabled.
Note: There is currently an edge case bug affecting IP whitelisting. This bug is on the docket to be fixed shortly.
5.1 – 2014-11-29
- Under the hood refactoring and clean up for performance and maintainability.
- Small visual refinements to the settings panel.
5.0.1 – 2013-01-27
- Does not block user activation page in network mode
5.0 – 2012-11-02
- WordPress 3.5 compatibility (3.5 eliminated the Privacy settings panel in favor of a refreshed Reading panel)
- Real validation (on the fly and on save) for IP address entries
- “Restriction message” now supports simple HTML and is edited using WordPress’s simple HTML tag editor
- A bunch of visual refinements that conform better with WordPress 3.4 and newer (spacing, native “shake” effect on invalid entries just like the login form, etc.)
- A bunch of under the hood refinements (e.g. playing nicer with current screen Help API)
4.0 – 2011-07-16
- New restriction option – show restricted visitor a specified page; use with custom page templates for great for website teasers!
- Major improvements to settings user interface, including hiding unused fields based on settings, easier selection of restriction type, and cleaner “remove” confirmation for IP address list
- Performance improvements – catches and blocks restricted visitors earlier in the loading process
- New filter hooks for other developers: ‘restricted_site_access_is_restricted’, ‘restricted_site_access_approach’, ‘restricted_site_access_redirect_url’, and ‘restricted_site_access_head’
- Localization ready – rough Spanish translation included!
- Basic support for no JavaScript mode
- Optimized for PHP 5.2, per new WordPress 3.2 requirements (no longer supports PHP < 5.2.4)
- Assorted other improvements and optimizations to the code base
3.2.1 – 2011-03-25
- Restored PHP4 compatibility
3.2 – 2011-03-25
- More meaningful page title in “Display Message” mode (previously WordPress > Error)
- Code clean up, prevent rare warnings in debug mode
3.1.1 – 2010-07-17
- Fixed PHP warning when debugging is enabled and redirect path is not checked
3.1 – 2010-07-11
- New feature: backwards compatibility with PHP < 5.1 (limited testing with earlier versions)
- Bug fix: disappearing blocked access message text box on configuration page
- Bug fix: login always redirects visitor back to correct page
- Improved: built in help on configuration page updated, clearer
- Improved: “IP already in list” indicator
- Improved: optimizations to code that handles restriction behavior
3.0 – 2010-07-05
- Integrates with Privacy settings page and site visibility option instead of adding a whole new page
- Simplified options: clearer instructions, removed unnecessary hiding / showing of some options, fewer lines
- Indicates whether the site is blocked in the admin next to the site title (WordPress 3.0+ only)
- New action hook,
restrict_site_access_handling, allowing developers to add their own restriction handling - Cleans up / removes settings when uninstalled
- Assorted under the hood improvements for best coding practices, sanitization of options, etc
2.1 – 2010-02-10
- Customize blocked visitor message
- Stronger security (patched “search” hole)
- Better display / handling of blocked visitor message
2.0 – 2010-01-10
- Add support for IP ranges courtesy Eric Buth
- Major UI changes and improvements; major code improvements
1.0.2 – 2009-10-13
- Fix login redirect to home; improve redirect handling to take advantage of wp_redirect function
1.0.1 – 2009-09-10
- Important fundamental change related to handling of what should be restricted
1.0 – 2009-08-17
- Added: Initial public release.